AWS ECS Manual Deployment Guide
This guide is intended for those who want to deploy a small part of the ECS infrastructure to support the Private AI solution, or for advanced users. It is recommended to use the Automated AWS ECS deployment guide for most use cases.
Note:
This guide is meant for ADVANCED users who are looking to customize their ECS components in their Private AI deployment. This guide walks through a security focused, component by component deployment and is NOT recommended for new users. If you are looking for the quickest way to deploy Private AI on AWS, please have a look at either our EKS Guide or our Automated ECS Guide
1. Prerequisites
Before you begin, you will need to install the AWS CLI and Docker tools.
Please also see our installation documentation for more information on how to retrieve the Private AI docker image.
2. Create VPC
AWS resources such as ECS are connected to a virtual private cloud. In order to segregate the Private AI cluster from the rest of your cloud deployment, it is preferable to create a new VPC. Check What is Amazon VPC for more details, or follow the instructions below.
Note:
The default VPC in AWS has special properties, and not all of this guide may be relevant. Check Default VPCs for more information.
- Navigate to the VPC Management Console.
- Click “Create VPC”.
- Select “VPC and more”.
-
Enter an Auto-generate tag.
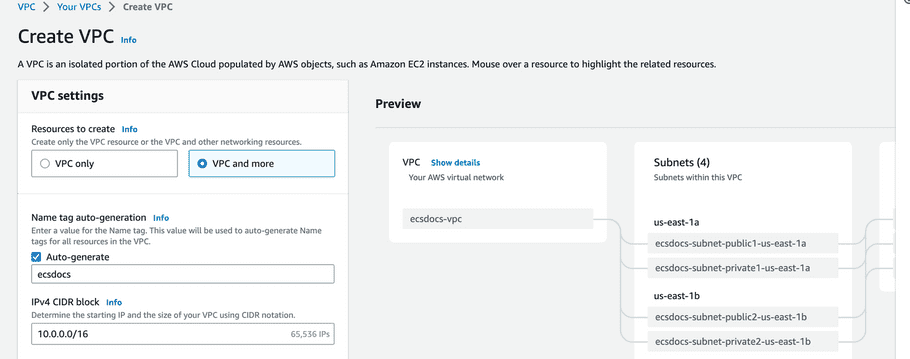
- Leave all other defaults.
- Click “Create VPC”.
Note:
Creation of the individual subnets, route tables, and network connections are beyond the scope of this article.
3. Policy Creation
In order to create and manage the Private AI cluster, we will create a new Policy with the minimum permissions to effectively manage the cluster with a single user.
Note:
If you have a production environment with segregation of duties, you may not want all permissions in a single policy.
- Navigate to the IAM Dashboard and click “Policies” on the left side.
- Click “Create Policy”.
- Click “Select a service” and search “Elastic Container Registry”.
-
Expand “Actions allowed”, you can select “All Elastic Container Registry actions (ecr:*)”.
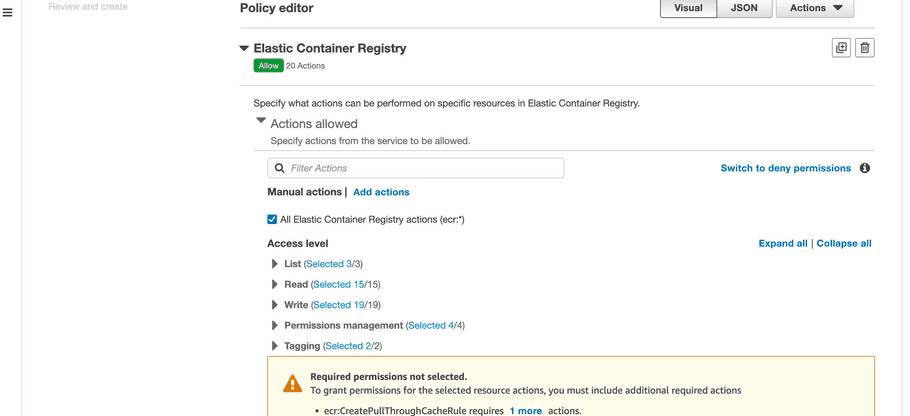
-
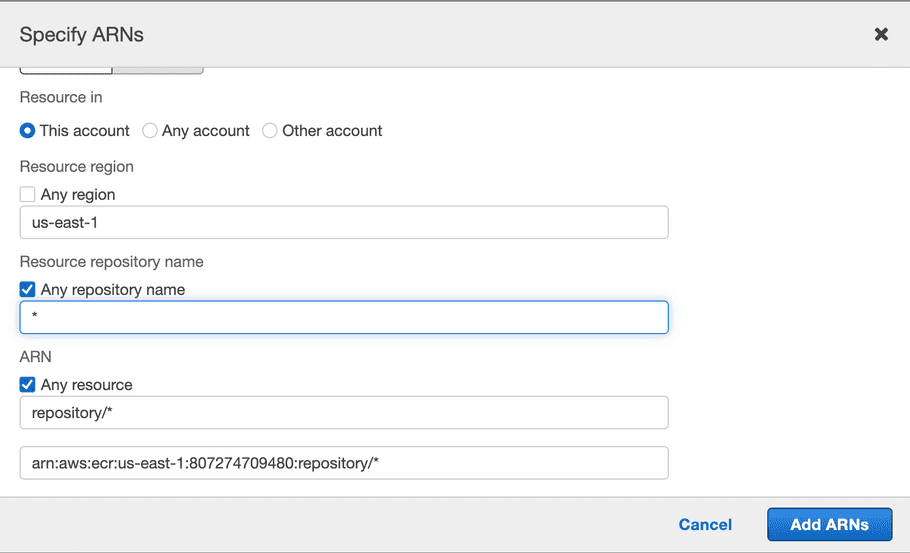
Expand “Resources”, select “This account”, “Add ARN” and specify the region your container will be hosted in. For example “us-east-1” or “ca-central-1”. Enter “*” for repository and click “Add ARNs”.
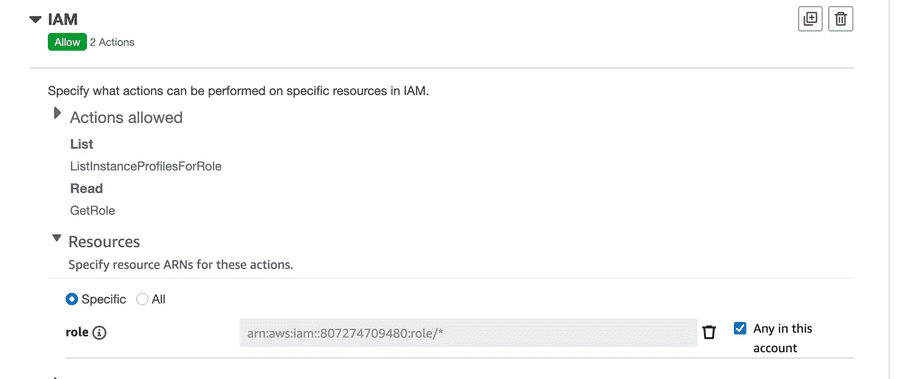
- Click “Add more permissions” and select the service “IAM”.
- Expand “List” select “ListInstanceProfilesForRole”.
- Expand “Read” select “getRole”.
-
Expand “Resources” and select “Any in this account” next to “role”.
- Click “Add more permissions” and select the service “CloudFormation”.
-
Expand “List” and select “ListStacks”.
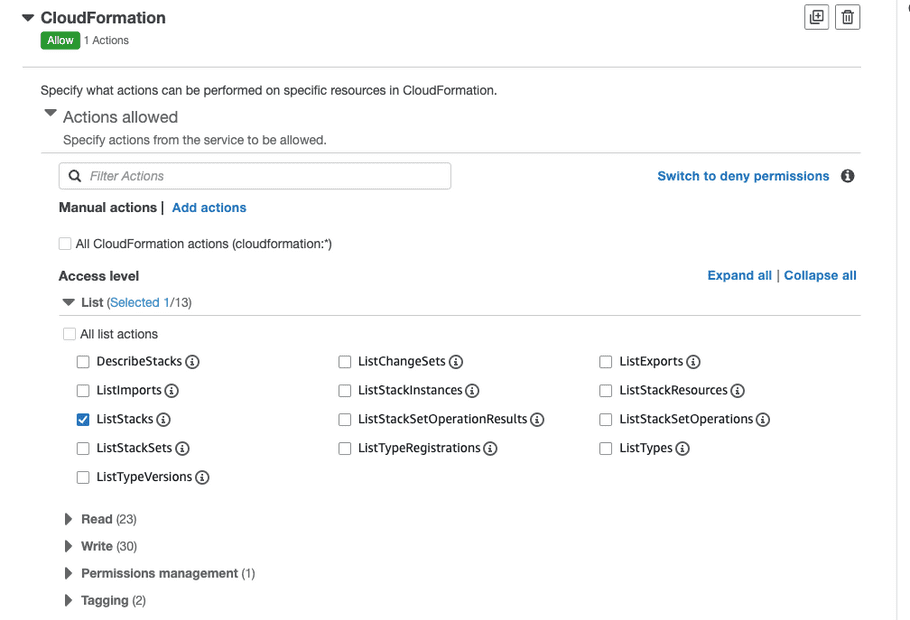
- Click “Add more permissions” and select the service “EC2 Auto Scaling”.
- Expand “Tagging” and select “CreateOrUpdateTags”.
-
Expand “Resources” and select “Any in this account” next to “autoScalingGroup”.
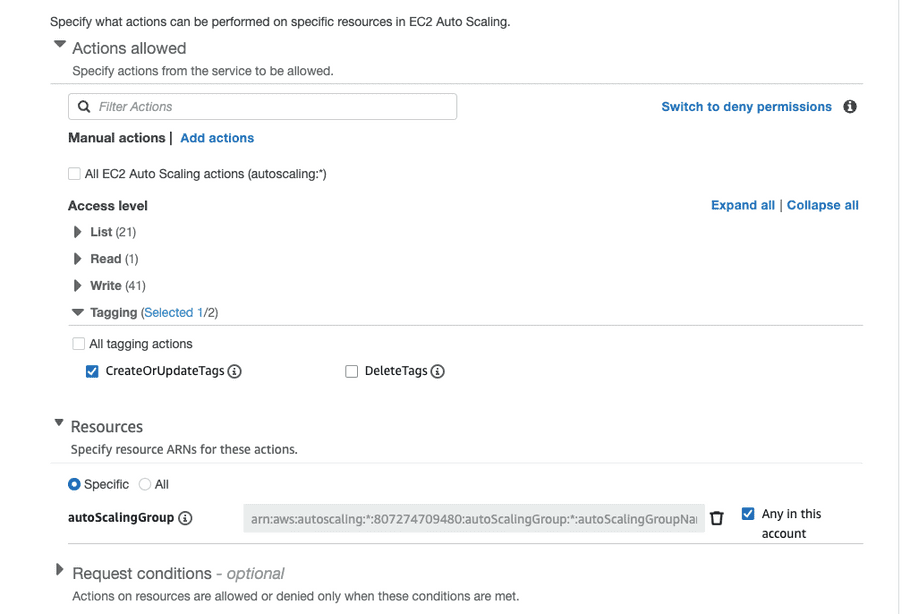
- Click “Add more permissions” and select “EC2”.
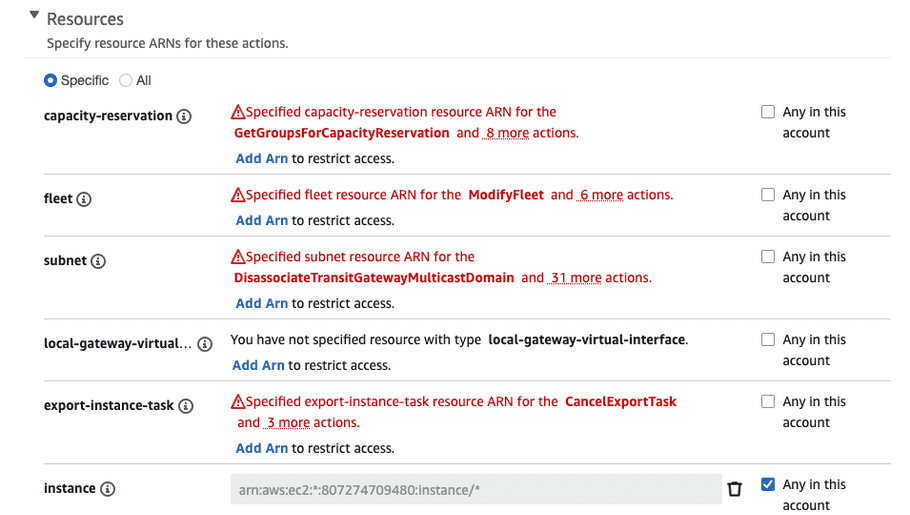
- Expand “Write” and select “AllocateAddress”, “AuthorizeSecurityGroupEgress”, “CreateLaunchTemplate”, “CreateLaunchTemplateVersion”, “CreateNatGateway”, “ModifyLaunchTemplate”, “RevokeSecurityGroupEgress”, “StartInstances”, “StopInstances”, and “TerminateInstances”.
- Expand “Tagging” and select “CreateTags”.
-
Expand “Resources” and select “Any in this account” next to the “elastic-ip”, “instance”, “launch-template”, “natgateway”, “security-group”, and “subnet” resources.
- Click “Add more permissions” and select “CloudWatch Logs”.
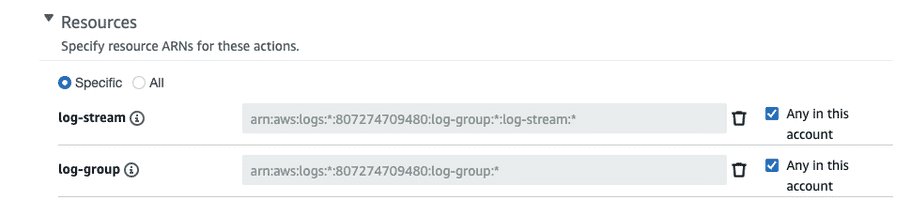
- Expand “List” and select “DescribeLogStreams”.
- Expand “Read” and select “GetLogEvents”.
- Expand “Write” and select “PutRetentionPolicy”.
-
Expand “Resources” and select “Any in this account” next to “log-stream” and “log-group”.
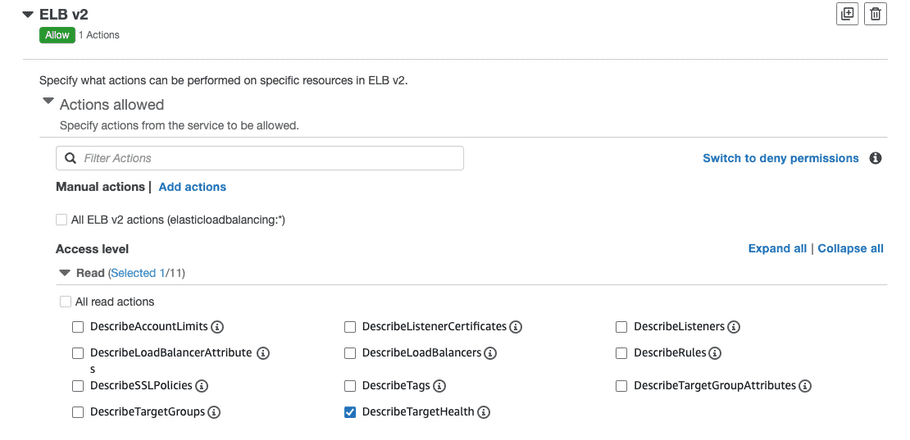
- Click “Add more permissions” and select “ELB v2”.
-
Expand “Read” and select “DescribeTargetHealth”.
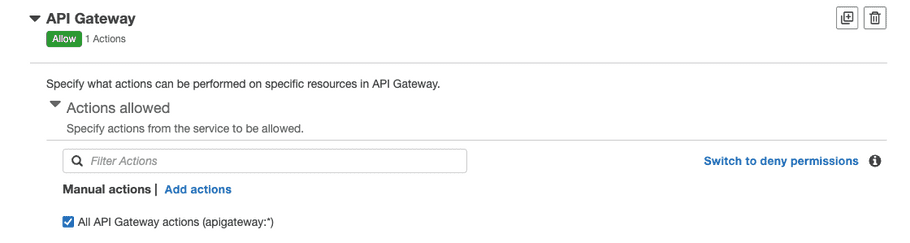
- Click “Add more permissions” and select “API Gateway”.
-
For “Actions allowed” check “All API Gateway actions”.
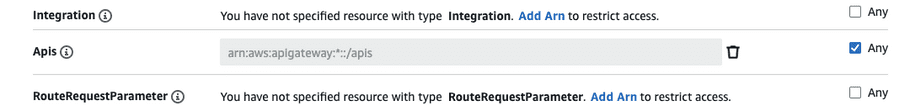
- Expand “Resources” and select “Any” next to “Account”, “RestApis”, “VpcLinks” and “VpcLink”.
- Click “Add more permissions” and select “API Gateway V2”.
- For “Actions allowed” check “All API Gateway V2 actions”.
-
Expand “Resources” and select “Any” next to “Api”, “Apis”, “IntegrationResponses”, “Routes”, and “Stages”.
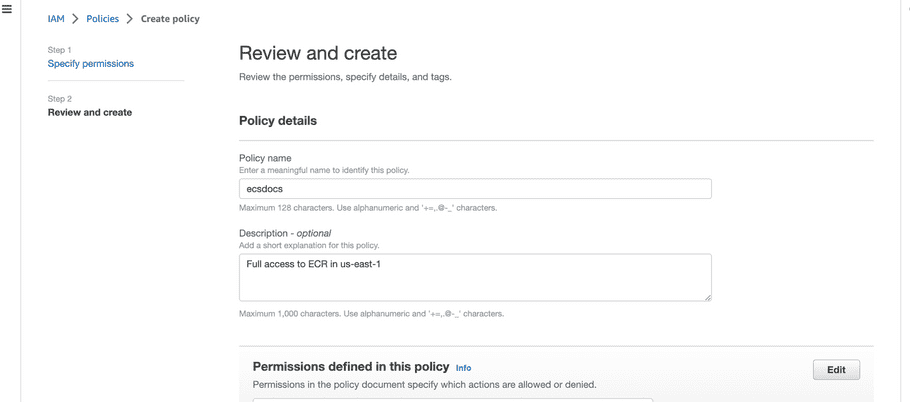
- Click “Next”.
-
Add a policy name and description that is representative of the permissions.
- Optional - Add tags as required.
- Click “Create Policy”.
The final policy is listed here:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "apigateway:*",
"Resource": [
"arn:aws:apigateway:*::/account",
"arn:aws:apigateway:*::/apis",
"arn:aws:apigateway:*::/apis/*",
"arn:aws:apigateway:*::/apis/*/integrations",
"arn:aws:apigateway:*::/apis/*/integrations/*/integrationresponses",
"arn:aws:apigateway:*::/apis/*/routes",
"arn:aws:apigateway:*::/apis/*/stages",
"arn:aws:apigateway:*::/restapis",
"arn:aws:apigateway:*::/vpclinks",
"arn:aws:apigateway:*::/vpclinks/*"
]
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "autoscaling:CreateOrUpdateTags",
"Resource": "arn:aws:autoscaling:*:807274709480:autoScalingGroup:*:autoScalingGroupName/*"
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": "cloudformation:ListStacks",
"Resource": "*"
},
{
"Sid": "VisualEditor3",
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupEgress",
"ec2:CreateLaunchTemplate",
"ec2:TerminateInstances",
"ec2:StartInstances",
"ec2:CreateNatGateway",
"ec2:CreateTags",
"ec2:RevokeSecurityGroupEgress",
"ec2:ModifyLaunchTemplate",
"ec2:StopInstances",
"ec2:AllocateAddress",
"ec2:CreateLaunchTemplateVersion"
],
"Resource": [
"arn:aws:ec2:*:807274709480:security-group/*",
"arn:aws:ec2:*:807274709480:natgateway/*",
"arn:aws:ec2:*:807274709480:launch-template/*",
"arn:aws:ec2:*:807274709480:subnet/*",
"arn:aws:ec2:*:807274709480:elastic-ip/*",
"arn:aws:ec2:*:807274709480:instance/*"
]
},
{
"Sid": "VisualEditor4",
"Effect": "Allow",
"Action": "ecr:*",
"Resource": "arn:aws:ecr:us-east-1:807274709480:repository/*"
},
{
"Sid": "VisualEditor5",
"Effect": "Allow",
"Action": [
"elasticloadbalancing:DescribeSSLPolicies",
"elasticloadbalancing:DescribeTargetHealth"
],
"Resource": "*"
},
{
"Sid": "VisualEditor6",
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:ListInstanceProfilesForRole"
],
"Resource": "arn:aws:iam::807274709480:role/*"
},
{
"Sid": "VisualEditor7",
"Effect": "Allow",
"Action": "logs:GetLogEvents",
"Resource": "arn:aws:logs:*:807274709480:log-group:*:log-stream:*"
},
{
"Sid": "VisualEditor8",
"Effect": "Allow",
"Action": [
"logs:DescribeLogStreams",
"logs:PutRetentionPolicy",
"apigateway:*"
],
"Resource": "arn:aws:logs:*:807274709480:log-group:*"
}
]
}4. Create IAM User
For the purpose of this article, we will use a single user account to create and manage all required Private AI cluster resources.
Note:
For production environments, you will likely want to separate these tasks into several individually named user accounts, or automatically build this environment using infrastructure-as-code checked into source control and deployed via a pipeline.
Note:
In a production environment, you will likely want to limit the permissions to ECS and EFS, and not use the “AmazonECS_FullAccess” and “AmazonElasticFileSystemFullAccess” policies directly.
- Navigate to the IAM Dashboard.
- Select “Users” from the left bar.
- Click “Add users” on the right side of the dashboard.
- Enter a username and select “Provide user access to the AWS Management Console - optional”.
-
Select “I want to create an IAM user”
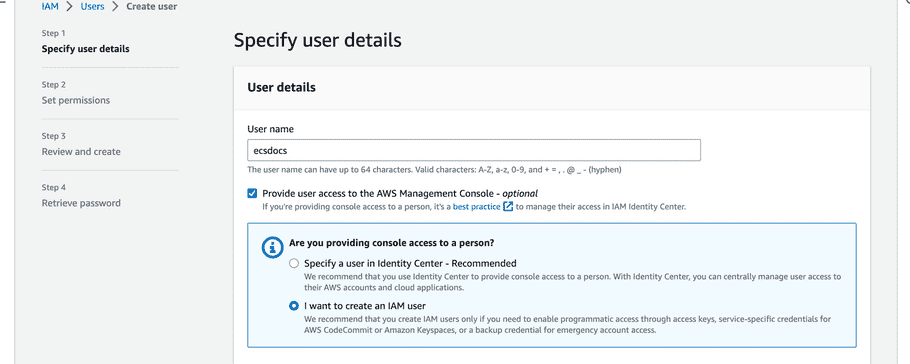
- Leave the defaults and click “Next”.
-
Select “Attach policies directly” and search for “AmazonECS
_
FullAccess” and select it.
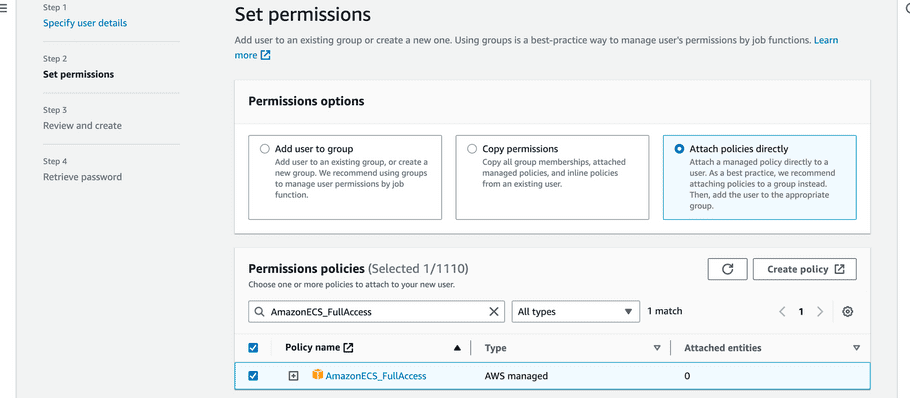
- Search for “AmazonElasticFileSystemFullAccess” and select it.
- Also search for the ECR policy we created in the previous section and select it.
- Click “Next”.
- Optional - Add tags as required.
- Click “Create”.
- Once your user is created and the policies attached to the user, log in to this account to continue the setup.
-
Ensure you change the region to the one entered in the policy in the previous steps.
-
Follow the
Create key pairs
guide to create an SSH key-pair for your account.
Note:
It is highly recommended to configure the account with MFA, which is beyond the scope of this article. Check Multi-Factor Authentication for more information.
5. Create ECR Repository and Upload Private AI Container
In order for an ECS cluster to start a task, the cluster must have access to the Private AI De-identification container. This can be accomplished by pulling the latest Private AI container, re-tagging it, and pushing it to the AWS Elastic Container Registry.
- Ensure you are logged into the IAM user from the previous steps.
- Navigate to the “Elastic Container Registry” dashboard and click “Create repository”.
- Select “Private”.
-
Enter a name for your repository.
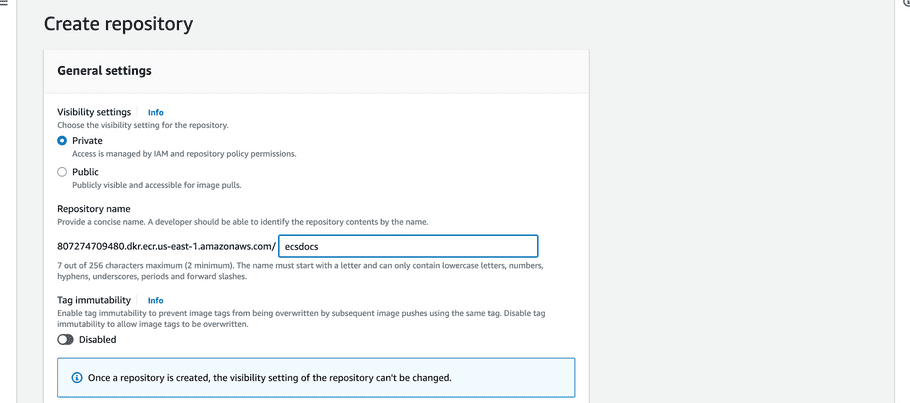
- Leave all other defaults and click “Create repository”.
-
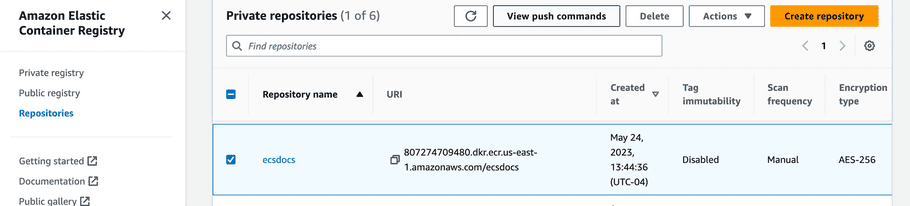
Select the repository from the list you just created and then click “View push commands” in the top right corner. A pop-up window should appear with copy-and-paste-able commands.
-
Copy the text from the first field under: “Retrieve an authentication token and authenticate your Docker client to your registry”. It should look like this:
aws ecr get-login-password --region <region> | docker login --username AWS --password-stdin <AWS URI> - Run this command at a terminal window.
- You should see Login Succeeded.
-
Verify that the Private AI image is loaded into Docker.
docker image ls REPOSITORY TAG IMAGE ID CREATED SIZE deid 3.3.2-cpu 561a5f6c2d62 12 days ago 8.45GB -
Tag the Private AI image to be uploaded to your AWS ECR repository.
docker tag deid:<version> <account-id>.dkr.ecr.<AWS region>.amazonaws.com/<repository name>:<version> -
Push the image to the ECR repository.
docker push <account-id>.dkr.ecr.<AWS region>.amazonaws.com/<repository name>:<version>
6. Create Security Groups
In order for the Private AI De-identification task to have the correct network connectivity, EC2 Security Groups must be created. These groups will allow inbound and outbound network connectivity for the EC2 host used for the ECS cluster, the EFS endpoint, and the Load Balancer. We will additionally create a security group for an EC2 bastion host, which can be used to managed the cluster, EFS, and provide troubleshooting.
Note:
If you are running the Private AI container in AWS FARGATE alone, some of these steps may not be needed.
-
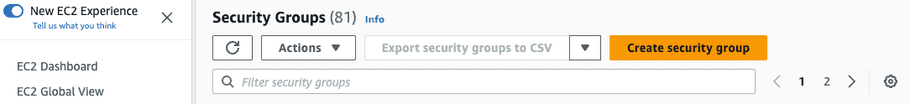
Navigate to the “EC2” dashboard and select “Security Groups” from the left side. Click “Create security group” to create a security group for the bastion host.
-
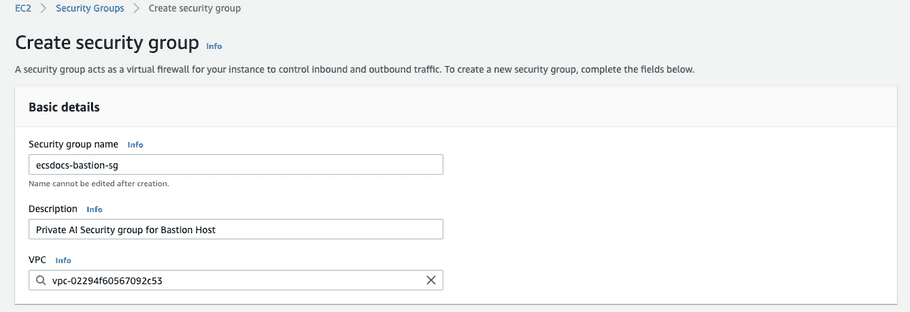
Enter the Security group name, Description, and VPC.
-
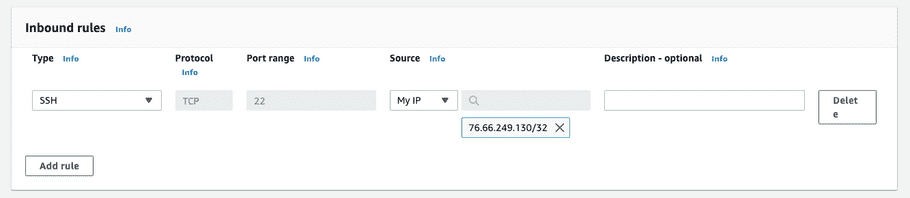
Add the following “Inbound rule” to allow SSH access from your current IP address.
-
Leave the default “Outbound rule”, which provides outbound access to anywhere.
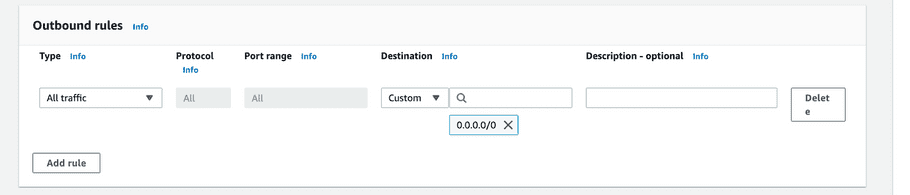
- Optional - Add tags as required.
- Click “Create security group”.
-
Navigate to the the “Security Groups” dashboard and click “Create security group” again to create a second security group for the ECS hosts.
-
Add the following two “Inbound rules”: one for HTTP access to the container, and one for SSH access from inside the VPC.
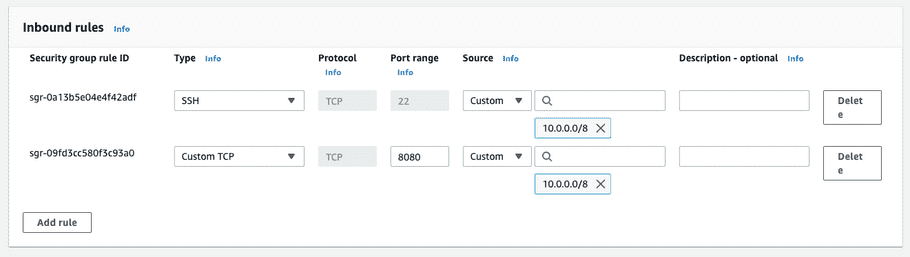
-
Leave the default “Outbound rule”, which provides outbound access to anywhere.
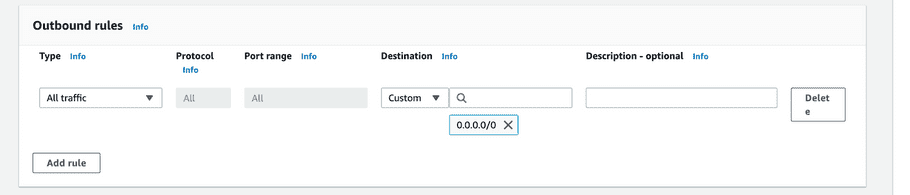
- Optional - Add tags as required.
- Click “Create security group”.
- Navigate to the the “Security Groups” dashboard and click “Create security group” again to create a third security group for access to the EFS mounts.
-
Enter the Security group name, Description, and VPC.
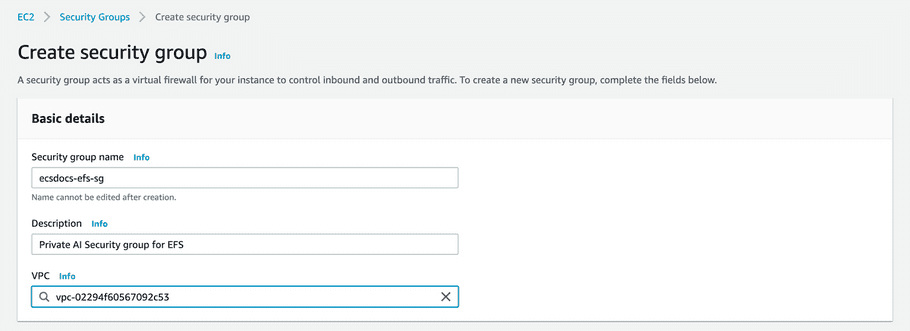
-
Add the following two “Inbound rules”: one to allow access from the ECS cluster to the EFS service and one to allow access from the bastion host to the EFS service.
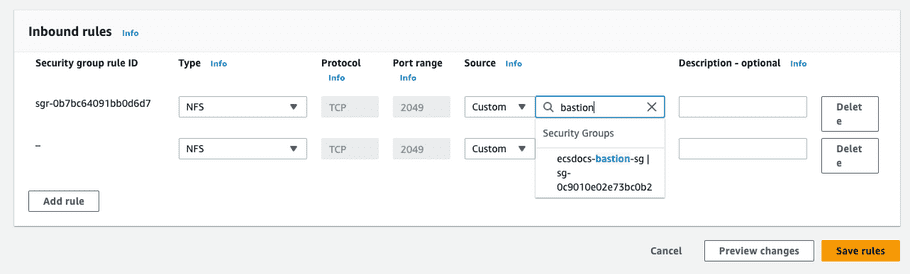
-
Leave the default “Outbound rule”, which provides outbound access to anywhere.
- Optional: Add tags as required.
- Click “Create security group”.
- Navigate to the the “Security Groups” dashboard and click “Create security group” again to create a fourth security group for the Load Balancer.
-
Enter the Security group name, Description, and VPC.
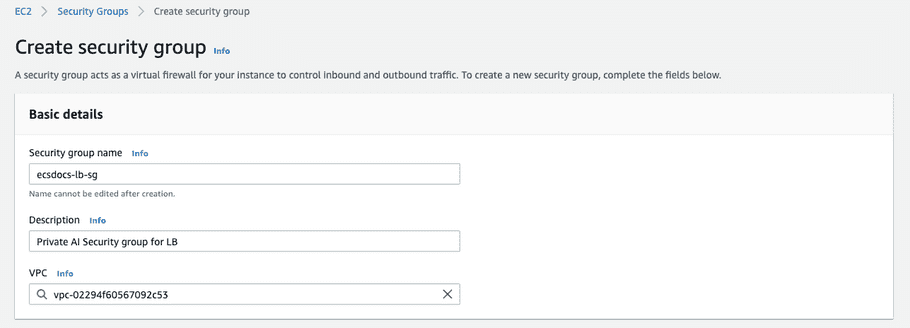
-
Add an “Inbound rule” to allow HTTP access from the VPC CIDR created in a previous section (
10.0.0.0/16) if you prefer an internal load balancer, or to allow HTTP from the Internet (0.0.0.0/0) if you prefer an internet-facing load balancer.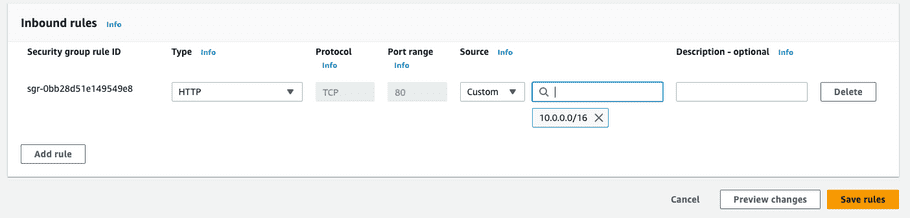
-
Remove the default “Outbound rule” and add a new rule to allow traffic to the instance on port 8080. Set the destination to the ECS security group created previously.
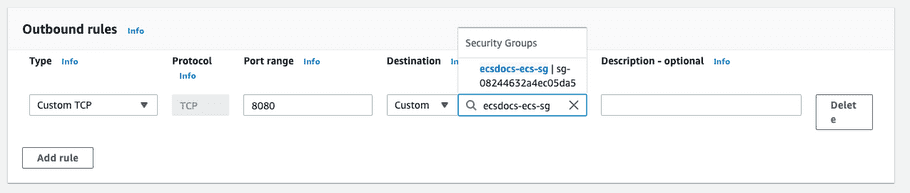
- Optional: Add tags as required.
- Search for and select the security group created for the ECS hosts in a previous step.
- From the bottom panel, select “Inbound rules” and click “Edit inbound rules”.
- Click “Add rule”.
-
Leave the default “Type” of “Custom TCP”, change the “Port” to 8080, and enter the “Source” of the security group for the load balancer created in a previous step.
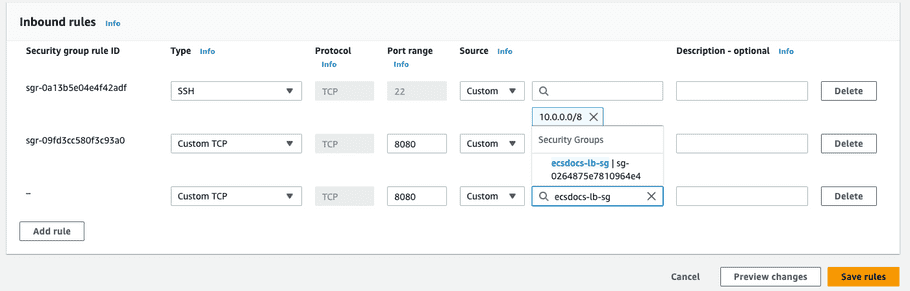
-
Click “Save rules”.
Note:
It is recommended for inbound and outbound traffic in a production environment be analyzed by your security team to match with your deployment strategy and risk posture.
7. Create EFS Mount
The Private AI De-identification service requires access to a license file on startup. If you are running an ECS cluster, each container must have access to the file. Mounting an EFS resource is one way to ensure the file is available to each container.
-
Navigate to the “EFS” dashboard and click “Create file system”.
-
Enter a name and select a VPC and then click “Customize”.
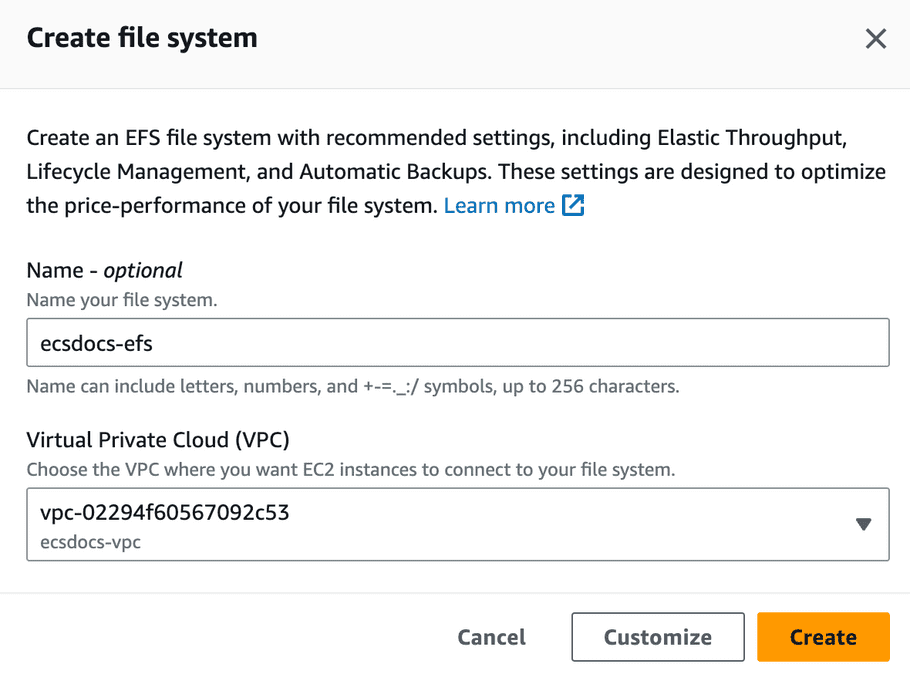
- For “File System Settings” leave all defaults and click “Next”.
-
For “Network” remove the default security groups add the previously created EFS security group for each Availability zone, and click “Next”.
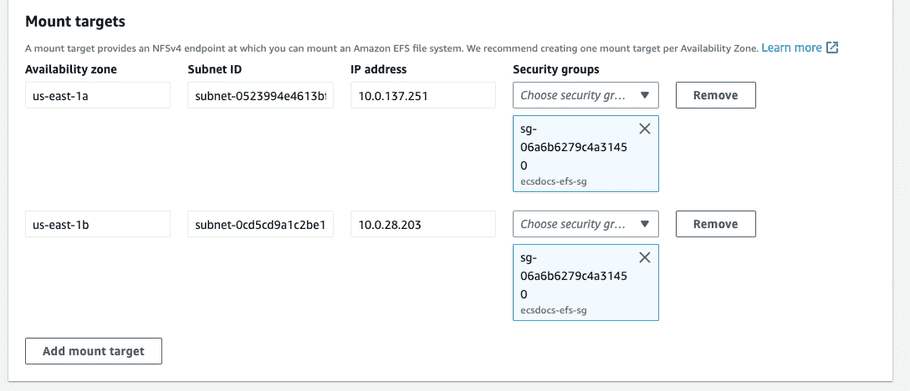
- Optional - For “File system policy - optional”, leave the default settings and click “Next”.
- For “Review and create”, click “Create”.
8. Create EC2 Launch Template
In order to provide EC2 hosts for the ECS cluster, an EC2 Launch Template is required.
- Navigate to the “EC2” dashboard and select “Launch Templates” on the left side.
- Click “Create launch template”.
-
Enter a name and description.
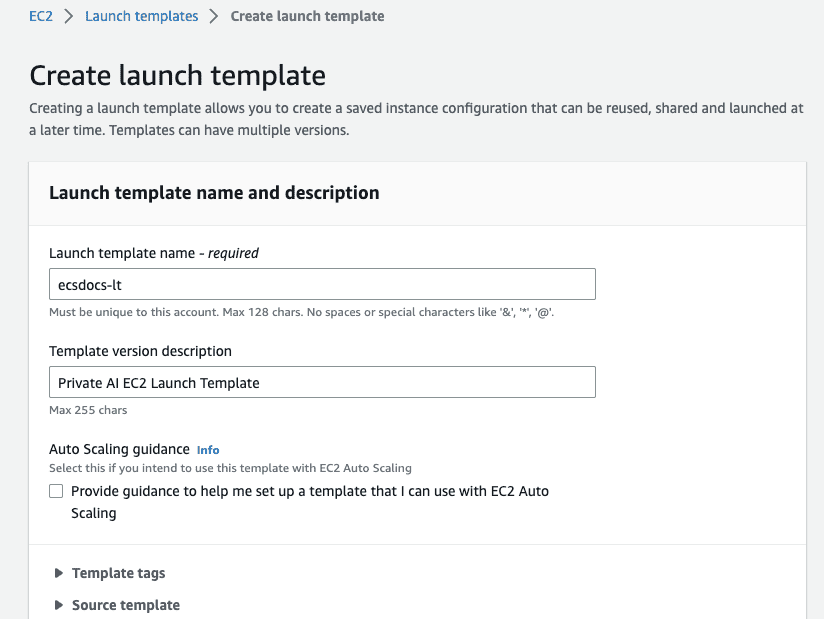
- Optional - Add template tags.
-
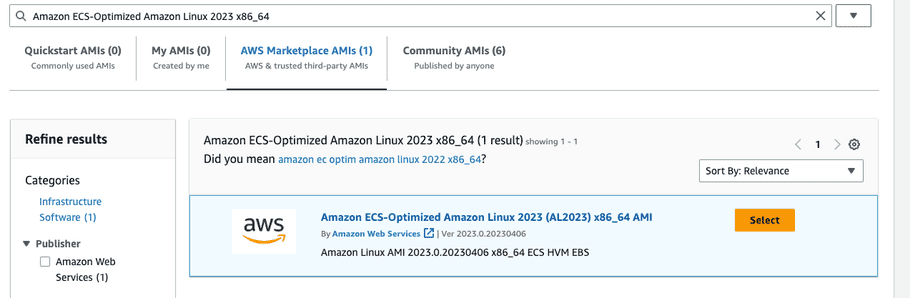
For “Application and OS Images (Amazon Machine Image)” search for Amazon ECS-Optimized Amazon Linux 2023 x86
_
64. Click the “AWS Marketplace AMIs” tab and click “Select” and “Continue”.
-
For “Instance type” select an appropriate instance type for your workload. For this document, we will use m5zn.xlarge since the ECS agent uses some of the host memory, this instance type is the optimal instance type for use with Private AI’s container. A 2 vCPU instance will give about 1.8M words per hour throughput. Image and PDF processing takes a lot more compute power, for which we recommend choosing a larger instance type such as the m5zn.3xlarge. Please refer to
Benchmarks
for more information.
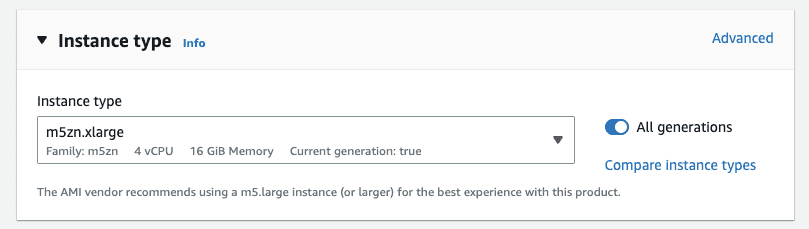
- For “Key pair (login)” include an SSH key pair if you wish to SSH into your EC2 instance. Key pair creation is beyond the scope of this document, but check Create key pairs for more information.
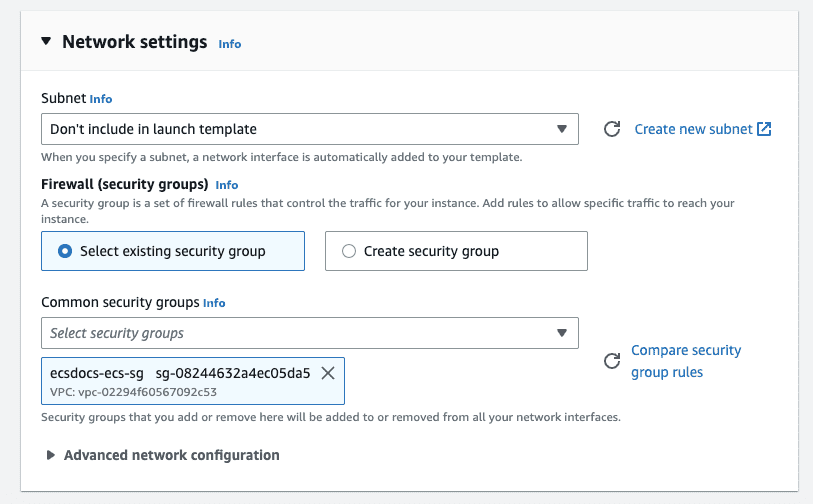
- For “Network settings” select “Don’t include in launch template” for “Subnet”.
-
For “Network settings” select “Select existing security group” and then select the security group previously created for the ECS cluster.
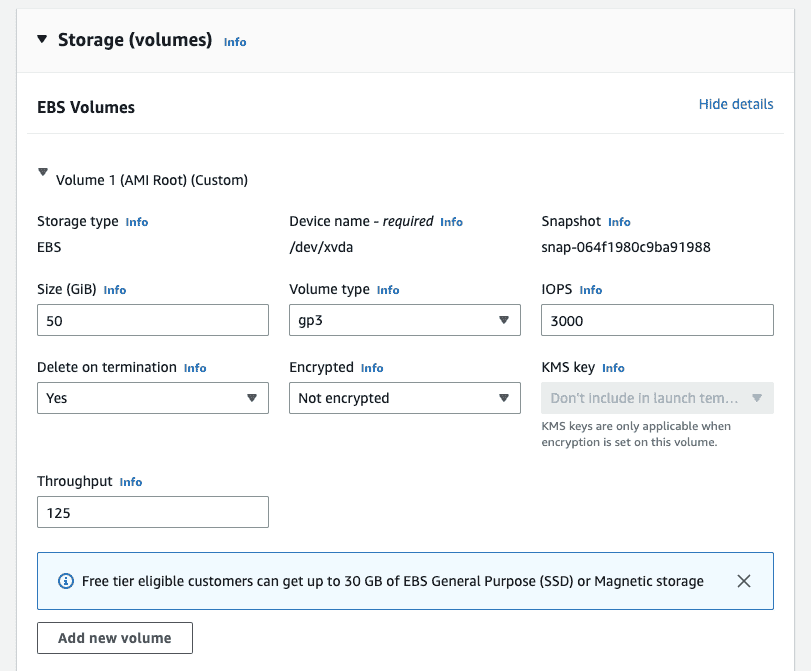
-
For “Store (volumes)” set the size to “50 GiB”.
- Optional - Add tags as required.
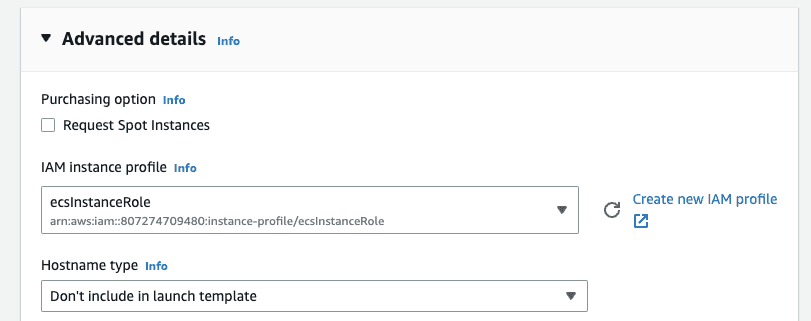
-
For “Advanced details” set the “IAM instance profile” to “ecsInstanceRole”.
Note:
If you do not have an ecsInstanceRole, check Amazon ECS container instance IAM role for more information. It should be automatically created the first time you visit the ECS dashboard.
-
For “Advanced details” also set the “User data - optional” to the following.
Note:
If you plan to change your cluster name in the future, be sure to add the same value here.
#!/bin/bash echo ECS_CLUSTER=ecsdocs-cluster >> /etc/ecs/ecs.config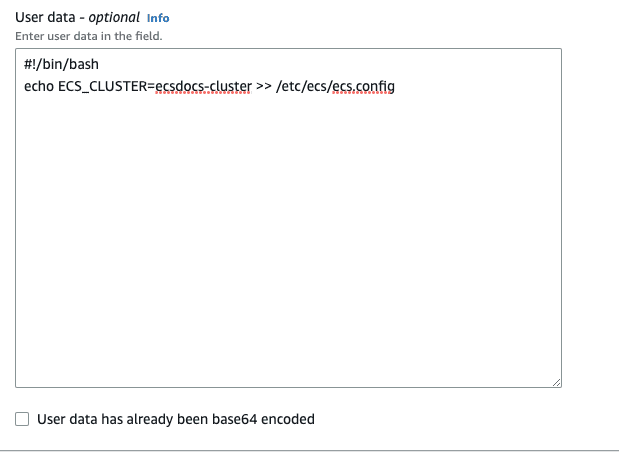
9. Create EC2 Target Group
In order to balance load across multiple ECS tasks, an EC2 target group is required.
- Navigate to the “EC2” dashboard and select “Target Groups” from the left menu.
- Click “Create target group”.
-
For “Basic configuration” select “IP addresses”.
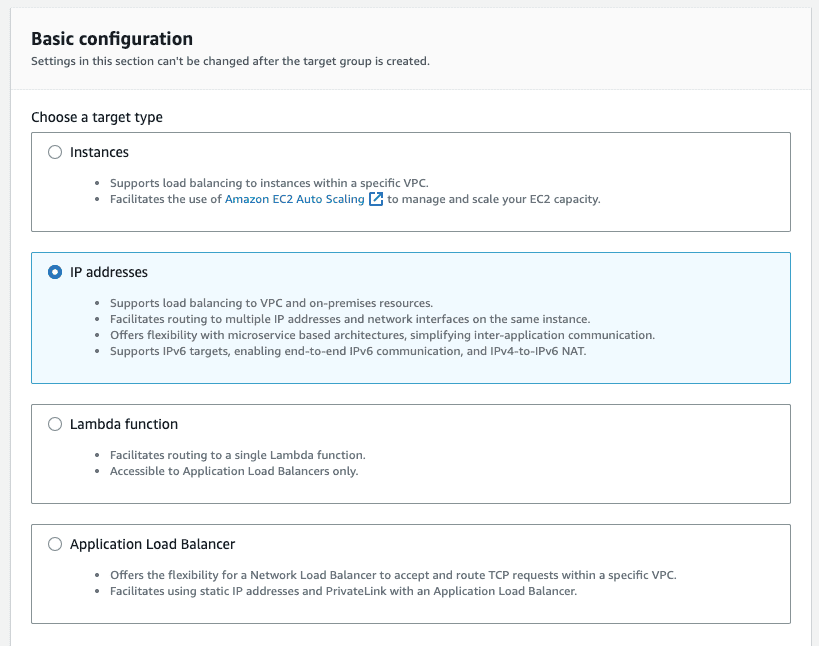
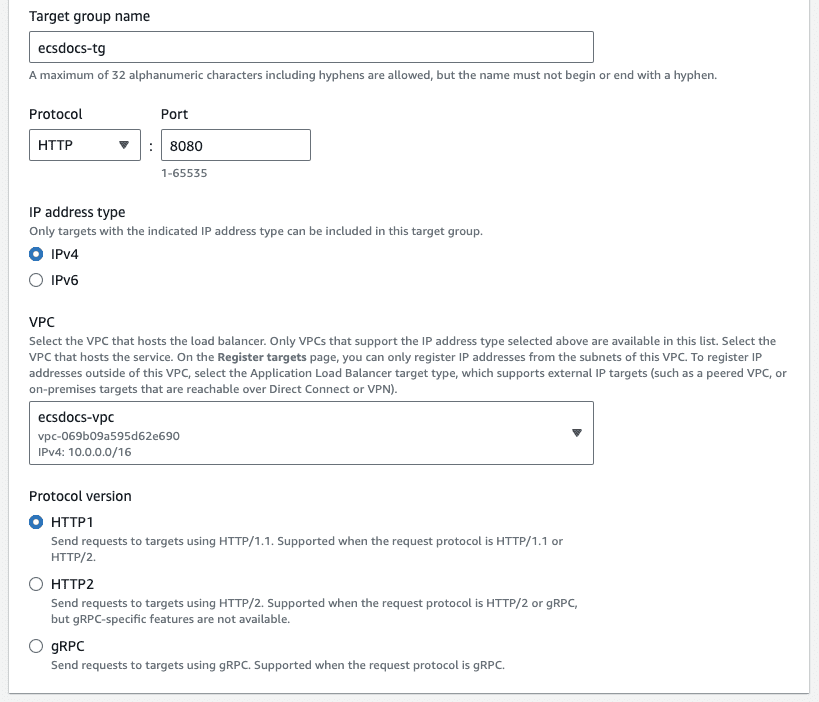
- Enter a target group name.
- Select the protocol “HTTP” and change the port to “8080”.
- For “IP address type” leave the default of “IPv4”.
- For “VPC”, select the previously created VPC.
-
Leave the “Protocol version” default of “HTTP1”.
- For “Health check protocol” leave the default of “HTTP”.
-
For “Health check path” enter
/healthz.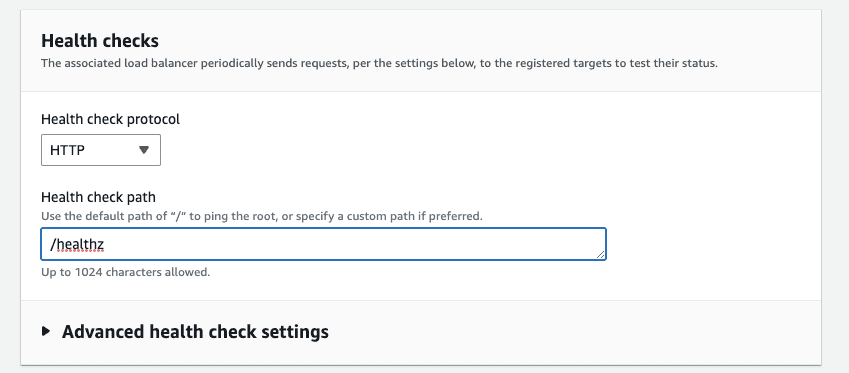
- Optional - For “Tags - optional” add any relevant tags.
- Click Next.
- Skip registering targets and click “Create target group”.
10. Create Load Balancer
In order to balance load across multiple ECS cluster tasks, a load balancer is required.
- Navigate to the “EC2” dashboard and select “Load Balancers” from the left menu.
- Click “Create load balancer”.
-
For “Load balancer types” select “Application Load Balancer” and click “Create”.
- For “Basic configuration” enter a unique name for the load balancer.
- If you plan on protecting the load balancer with an API Gateway, for “Scheme” select “Internal”. Otherwise select “Internet-facing”.
-
Leave the default “IP address type” of “IPv4”.
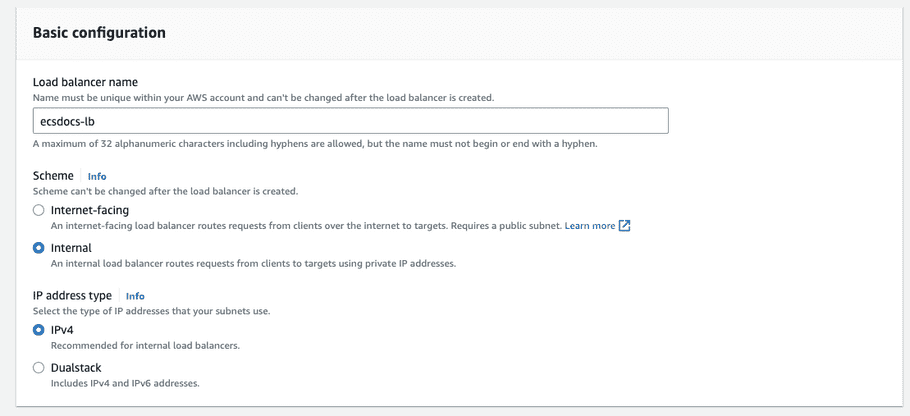
- For “Networking” select the VPC created in a previous section.
-
Check the box beside each availability zone and select the appropriate subnet depending on if you are deploying Internet-facing or Internal.
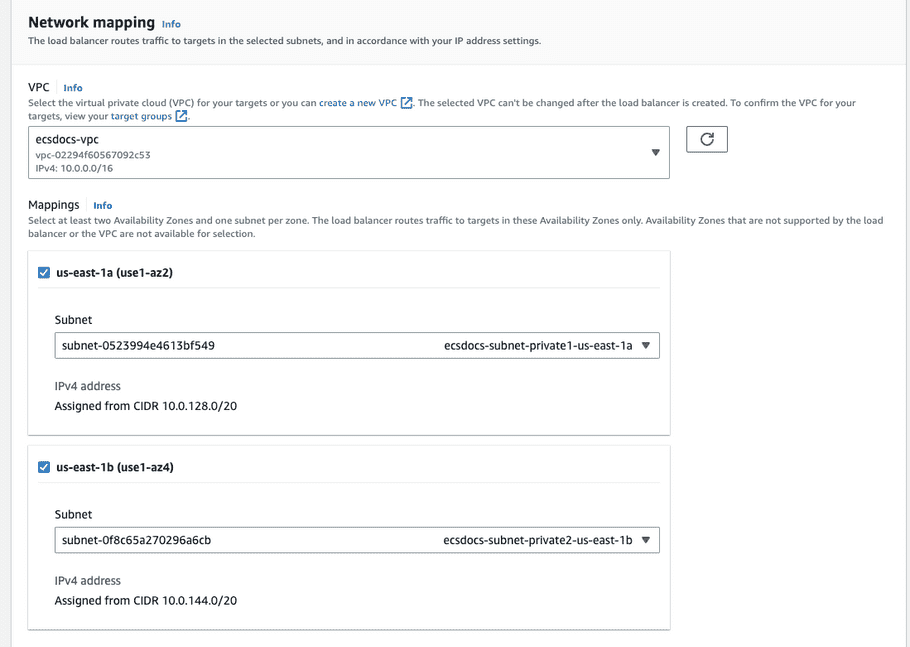
-
For “Security groups” select the previously created security group for the load balancer.
-
For “Listeners and routing” under “Protocol” select “HTTP” and change the “Default action” to the target group created in a previous section.
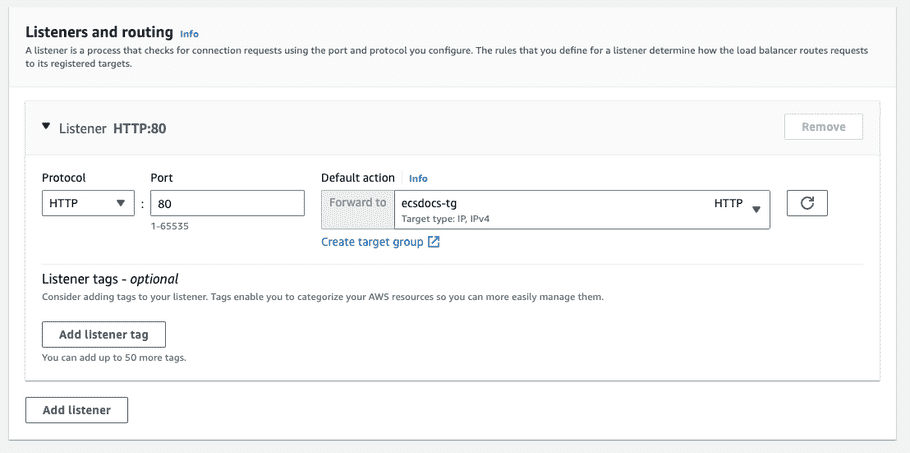
Note:
For production environments, it is recommended to provision SSL certificates, especially in Internet-facing scenarios. Creation and maintenance of SSL certificates are beyond the scope of this document. Check Create an HTTPS listener for your Application Load Balancer for more information.
- Optional - For “Add-on services - optional” and “Load balancer tags - optional” select appropriate settings.
- Review the summary and then click “Create load balancer”.
11. Create Auto Scaling Group
In order to use EC2 instances as hosts for the ECS cluster follow the steps below.
- Navigate to the “EC2” dashboard and select “Auto Scaling Groups” from the left menu.
- Click “Create an Auto Scaling group”.
-
Enter a name and select the launch template created in the previous step.
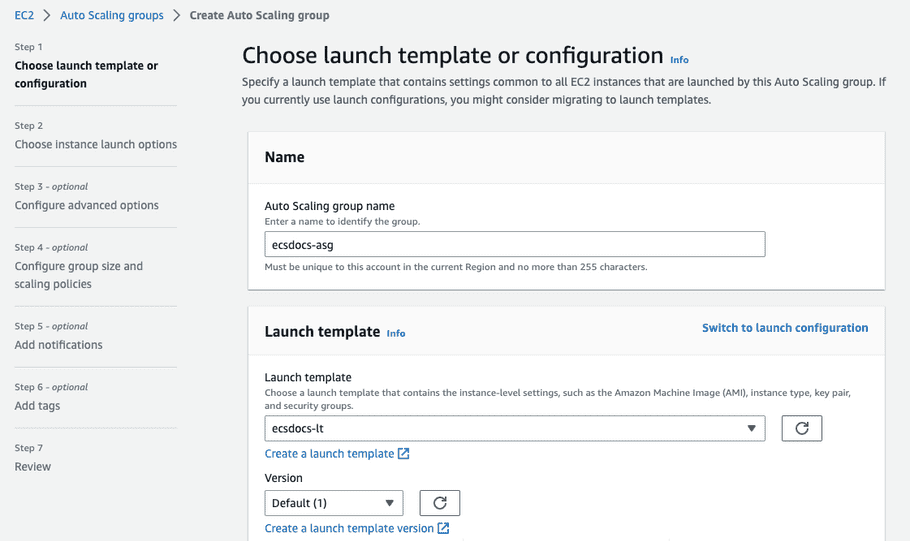
- Click “Next”.
- For “Network” select the VPC created previously.
-
Select the private subnets created in the previous steps.
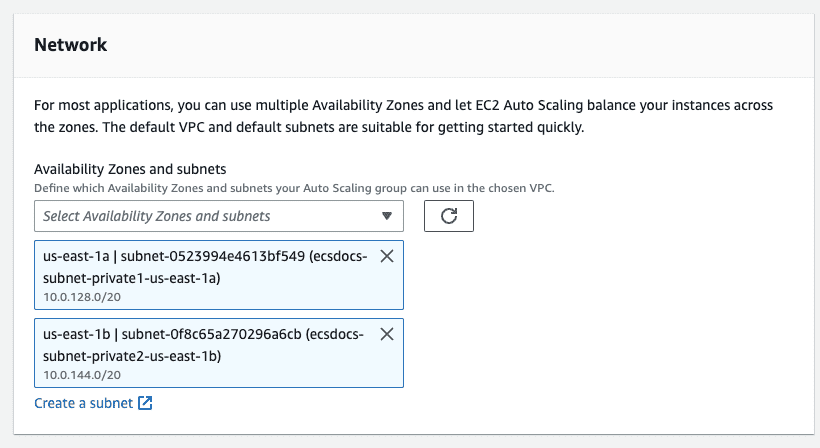
- Click “Next”.
-
For “Load balancing” select “No load balancer”.
Note:
We will be using the load balancer created in a previous section for the ECS Service Tasks, not for the EC2 instances directly.
- For “VPC Lattice integration options” leave the default “No VPC Lattice service”.
- Optional - For “Additional settings” optionally enable CloudWatch monitoring and instance warmup as required.
- Click “Next”.
-
For “Group size - optional” set the “Minimum capacity” to “0” and leave the other defaults at 1.
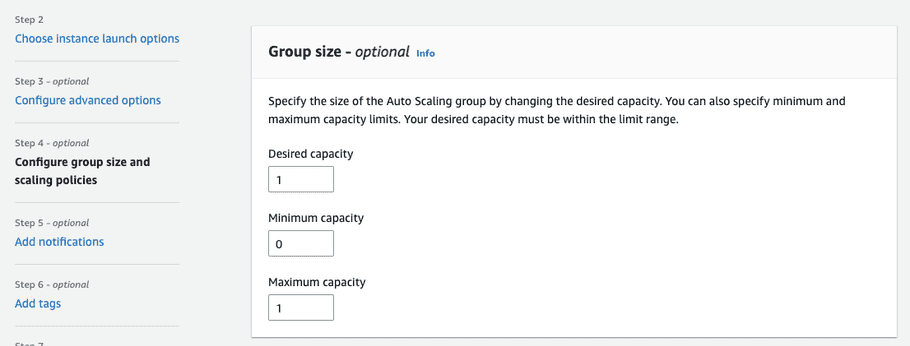
Note:
These settings are heavily dependent on your workload and performance, and must be tuned appropriately.
- Optional - For “Scaling policies - optional” leave the defaul of “None” or optionally create a scaling policy.
- Optional - For “Instance scale-in protection - optional” leave the default of unchecked or optionally enable scale in protection.
- Click “Next”.
- Optional - For “Add notifications - optional” configure an SNS topic.
- Click “Next”.
- Optional - For “Add tags - optional” add any relevant tags.
- Click “Next”.
- Review the configuration and click “Create Auto Scaling group”.
12. Create VPC NAT Gateway
If you have created a non-default VPC, your EC2 instances will not have access to the Internet from the private subnet. Alternatively, you can create an Internet Gateway. Check Connect to the internet using an internet gateway for more information. Consult with your security team to further restrict the instances' egress network access.
- Navigate to the “VPC” dashboard and select “NAT gateways” from the list on the left.
- Click “Create NAT gateway”.
-
Enter a name and select one of the public subnets created in a previous step.
Note:
If you select a private subnet, the NAT gateway will not have access to Internet traffic.
- Select “Connectivity type” of “Public”.
-
Click “Allocate Elastic IP” to create and allocate a public-facing IP address.

- Optional - Add tags.
- Click “Create NAT gateway”.
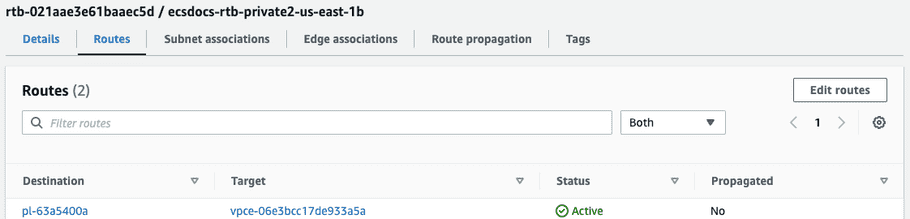
- Navigate to the “VPC” dashboard and click on “Route tables” from the list on the left.
- Click on one of the private subnets created in an earlier step and select “Routes” from the bottom section.
-
Click “Edit routes”.
- Click “Add route”.
-
For “Destination” select
0.0.0.0/0for all outbound access. -
For “Target” select “NAT Gateway” and select the previously created gateway from the steps above.
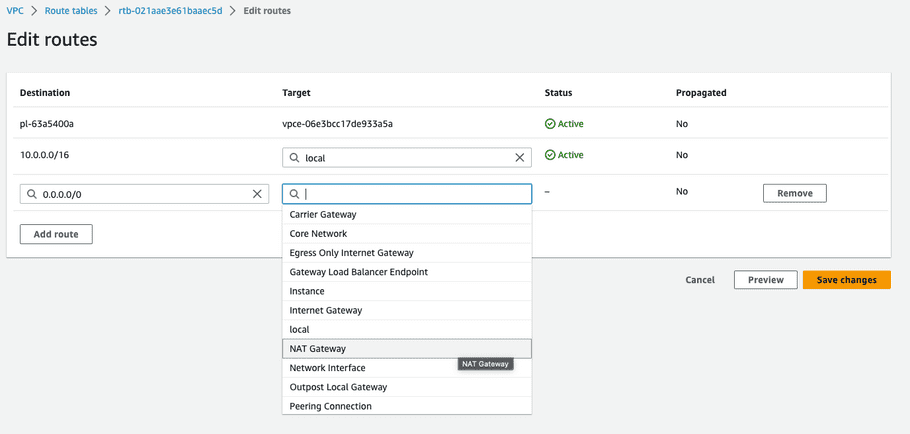
- Click “Save changes”.
-
Repeat adding the NAT Gateway route for the other private subnet.
Note:
For environments with high availablity requirements, consider adding a second NAT Gateway in an alternate availability zone.
13. Create ECS Cluster
-
Navigate to the “Elastic Container Service” dashboard and select “Clusters” from the left side. Click “Create Cluster”.
-
Enter the cluster name.
Note:
You must specify the same cluster name as you entered in the EC2 Launch Template - User Data section in a previous step.
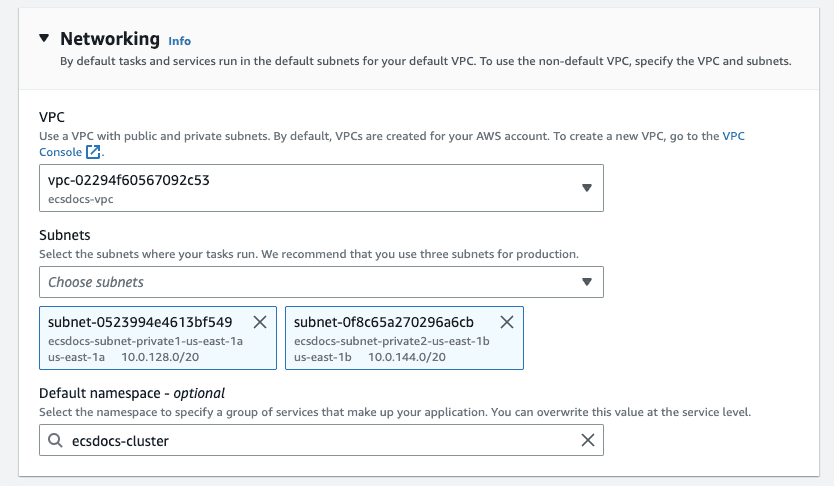
- Select the VPC where you would like to deploy the cluster.
-
Select the private subnets created in a previous step.
-
For “Infrastructure”, check the “Amazon EC2 instances” checkbox.
Note:
“AWS Fargate (serverless)” is only suitable for cost-optimized deployments.
-
For “Amazon EC2 instances”, select the “Auto Scaling group” we created in the previous optional step.
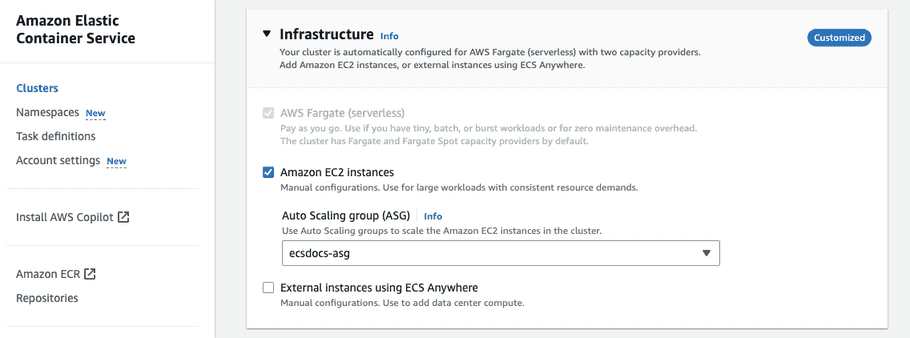
- Optional - For “Monitoring - optional” enable container insights if you would like to monitor usage of container resources. This is recommended for production configurations.
- Optional - For “Tags - optional” add any relevant tags.
- Click “Create”.
14. Create Bastion and Create License
In order to add a file to the new EFS file system and troubleshoot any clustering issues, we will create an EC2 instance to serve as our Bastion Host.
- Navigate to the “EC2” dashboard and click “Launch instance”.
- Enter a name for the EC2 instance.
- For “Application and OS Images” leave the default “Amazon Linux 2023 AMI”.
-
For “Architecture” select “64-bit (x86)”.
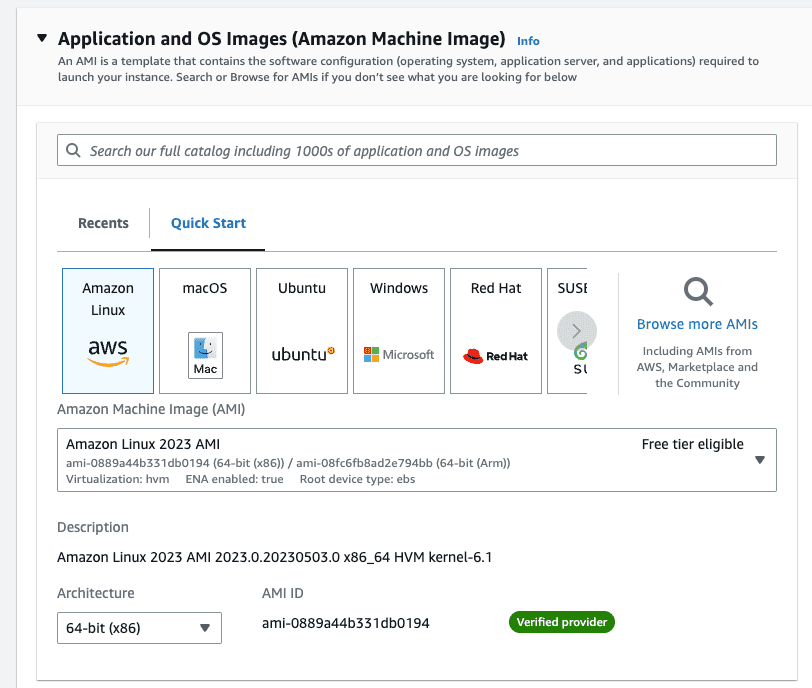
- For “Instance type” leave the default “t2.micro”.
-
For “Key pair” select an appropriate SSH key to connect to the EC2 instance.
Note:
Creating an SSH key is beyond the scope of this document. Check Create key pairs for more information.
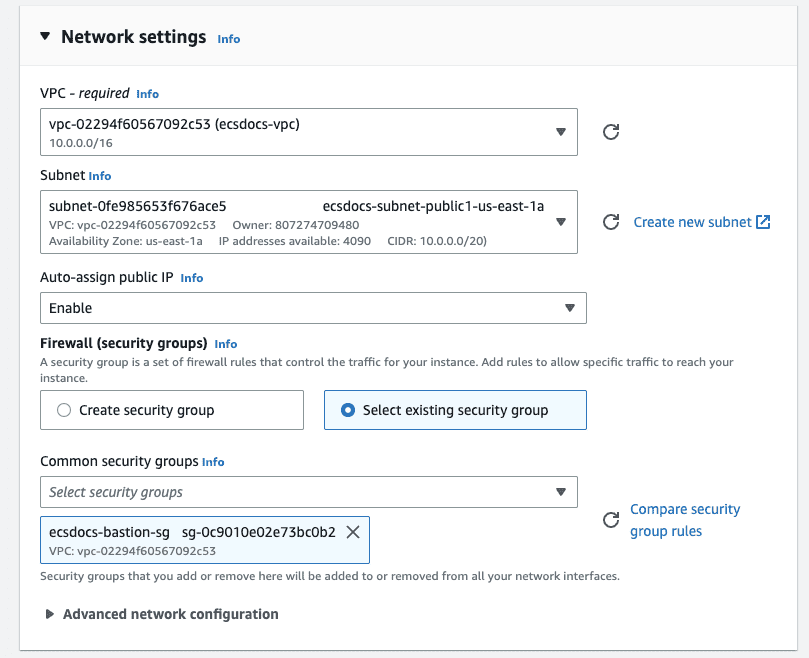
- For “Network settings” click “Edit”.
- Change the VPC to the one created in a previous section.
- For “Subnet”, select an available subnet that is publicly accessible and has an EFS mount created in a previous step.
- For “Auto-assign public IP” select “Enable”.
-
For “Firewall (security groups)” select “Select existing security group” and select the previously created security group for the bastion host.
- For “Configure storage” click “Advanced”.
- For “File systems” click “Show details”.
-
Click “Add shared file system”.
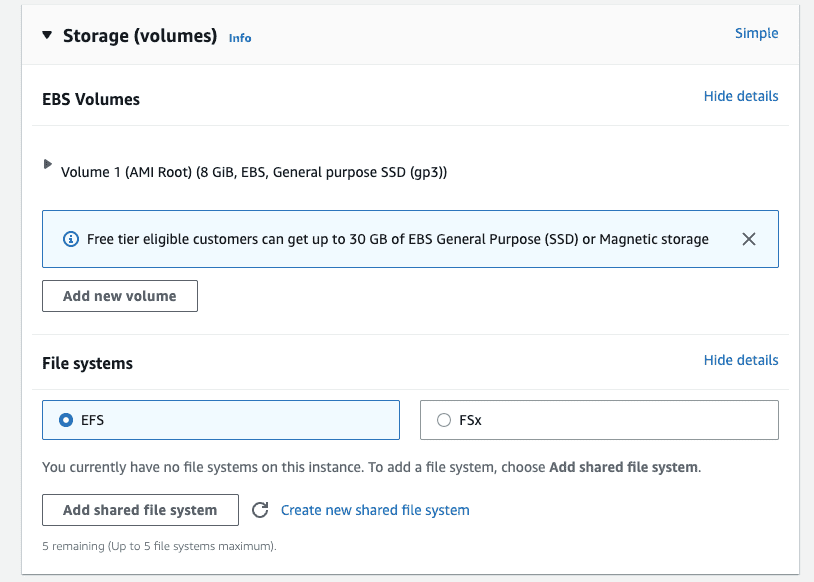
- For “File system” select the EFS file system created in the previous step.
-
Uncheck “Automatically create and attach security groups”. Leave all other defaults.
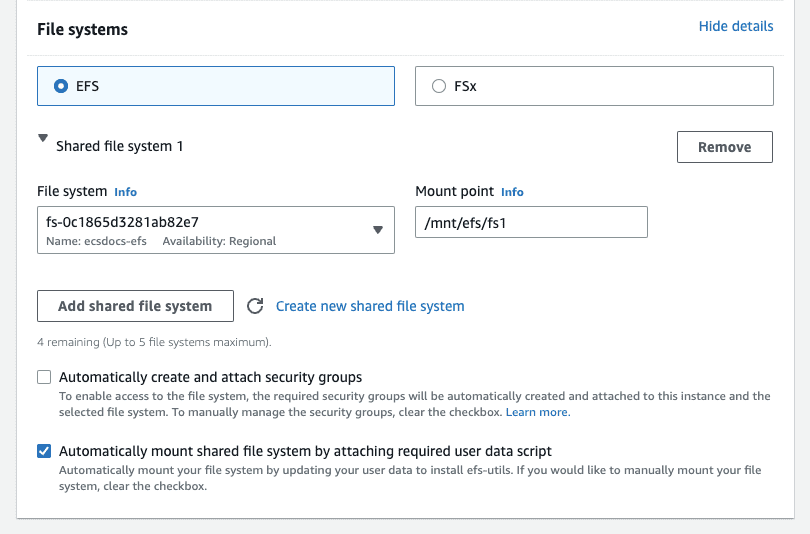
- For “Summary” review the information and click Launch instance.
- Navigate to the “EC2” dashboard and click “Instances” from the left, and then locate the newly created instance.
- Once the instance has started, log into it via SSH. The mechanism to do this is beyond the scope of this document. Check Connect to your Linux instance using SSH for more information.
-
Navigate to the EFS share and create a license file using the following commands.
cd /mnt/efs/fs1 sudo touch license.json sudo vi license.json - Paste the contents of your license.json file into the file.
-
Run the
exitcommand from the SSH terminal to close the session.Note:
There are multiple ways to manage files on an EFS filesystem, which are beyond the scope of this document.
15. Create ECS Task Definition
In order to run the Private AI De-identification container, ECS requires a task definition to find the image, allocate the correct resources, etc. Follow the steps below to create the ECS Task Definition.
-
From the Elastic Cluster Service dashboard, select “Task definitions” and click “Create new task definition”.
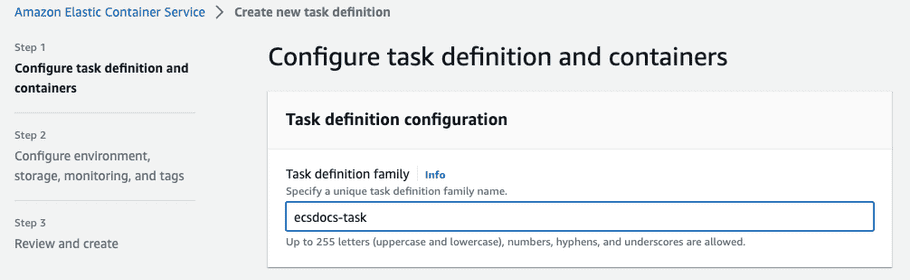
-
Enter a task definition family name.
- For Infrastructure requirements uncheck AWS Fargate and check Amazon EC2 instances.
- Leave the Operating system/Architecture as "Linux/X86_64" and Network mode as "awsvpc".
- For Task size set the CPU to "1 vCPU" and Memory to "14 GB".
-
For Task role and Task execution role select "ecsTaskExecutionRole".
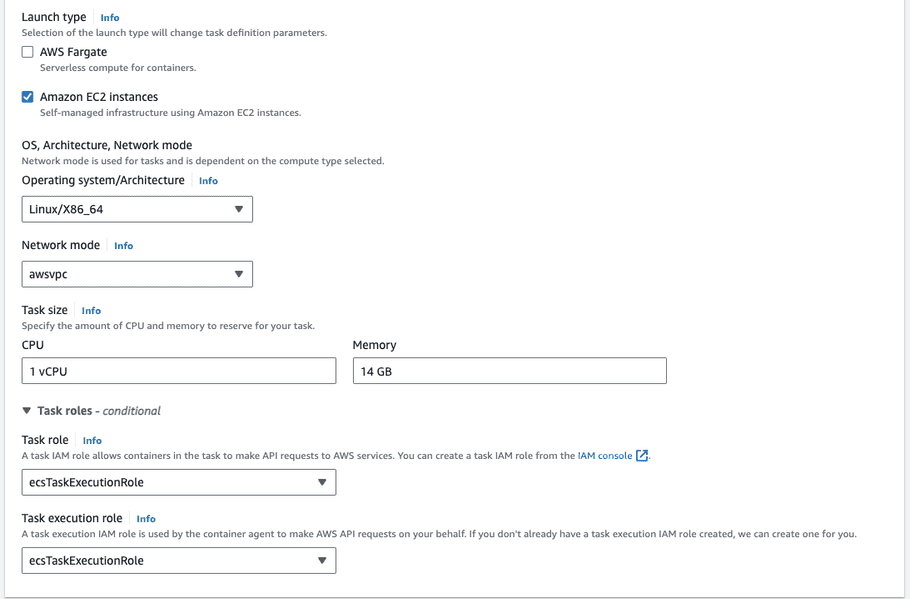
Note:
If the ecsTaskExecutionRole does not exist, follow the Amazon ECS task execution IAM role guide.
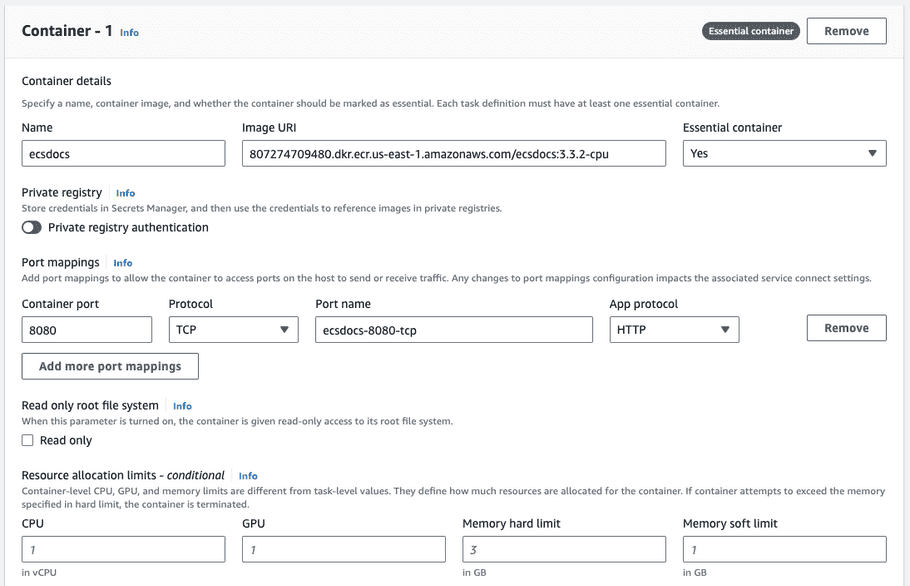
- For Container - 1, enter a Name and the Image URI created in a previous step, and set Essential container to "Yes".
- Enter a Container port of "8080", Protocol of "TCP", and App protocol of "HTTP".
-
Leave the Resource allocation limits - conditional empty. We will allow the container to consume all resources available to the task.
- For Environment variables - optional, leave the section empty.
-
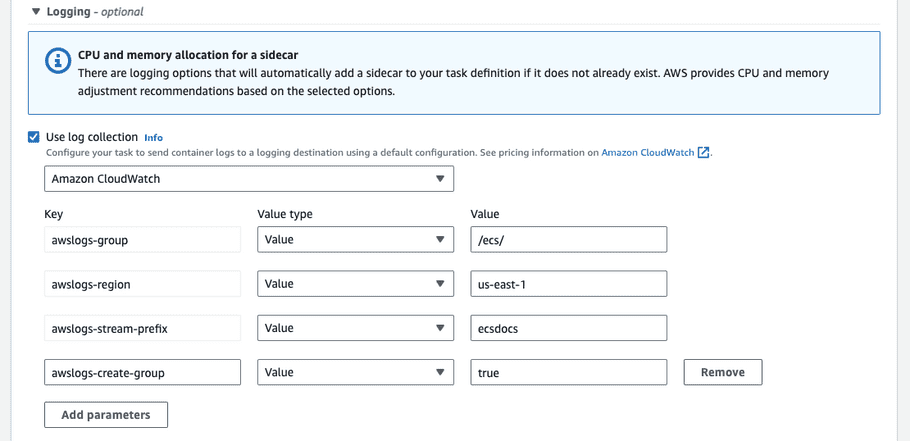
For Logging, optionally enable log collection. Sample values are depicted below.
Note:
If you plan to have CloudWatch Log Groups automatically created, you must add the "CloudWatchLogsFullAccess" policy to the "ecsTaskExecutionRole". Follow the Adding and removing IAM identity permissions guide.
-
For HealthCheck, enter the following details. The command is
CMD-SHELL, curl -f http://localhost:8080/healthz || exit 1for the health check, “Interval” is30, “Timeout” is5, “Start period” is60, and “Retries” is3.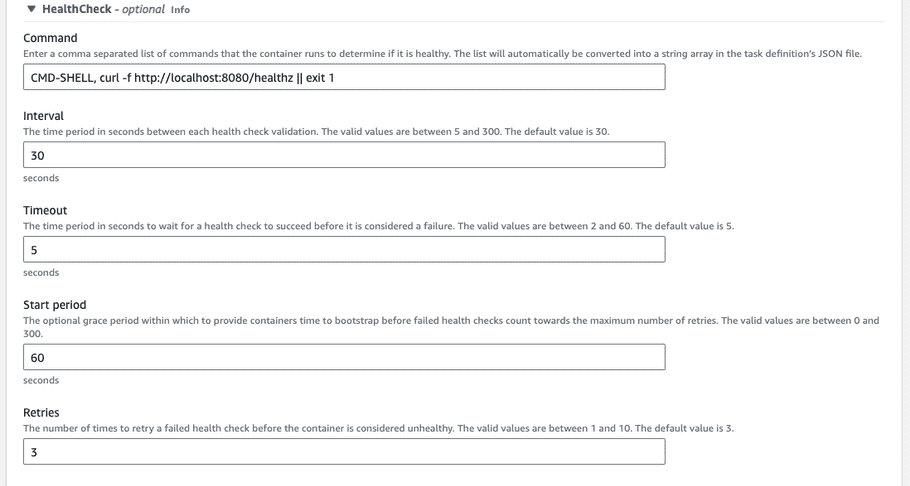
- Leave Container timeouts, Docker configuration, Resource limits (Ulimits), and Docker labels empty.
-
For storage, select "EFS" for the Volume type, enter a Volume name, select the File system ID created previously, and leave the Root directory and Access point ID as default.
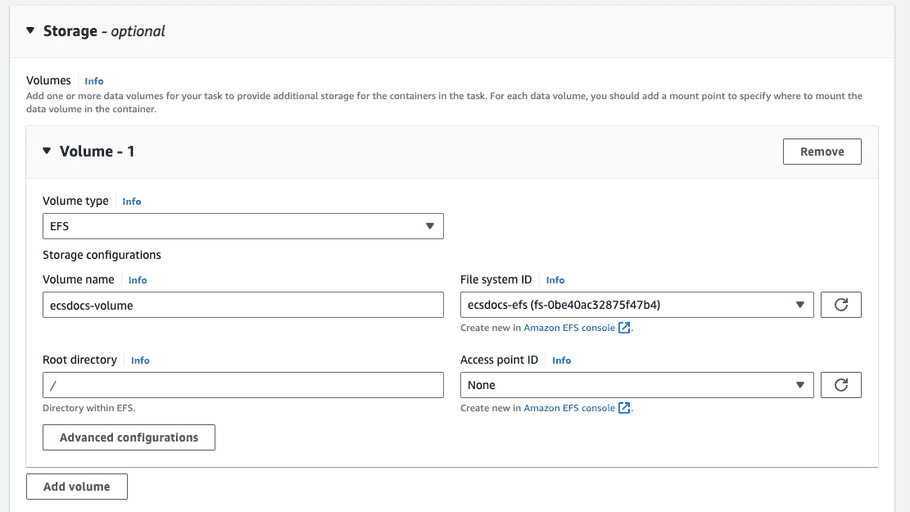
- Click "Add mount point".
-
Select the Container and Source volume created previously, enter a Container path of
/app/licenseand check the Read only box.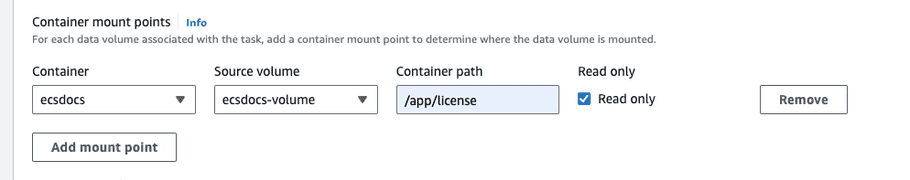
- For Monitoring and Tags, optionally set your desired configuration.
- Click create.
This is a sample of the container definition.
{
"taskDefinitionArn": "arn:aws:ecs:us-east-1:807274709480:task-definition/ecsdocs-task:1",
"containerDefinitions": [
{
"name": "ecsdocs",
"image": "807274709480.dkr.ecr.us-east-1.amazonaws.com/ecsdocs:3.3.2-cpu",
"cpu": 0,
"portMappings": [
{
"name": "ecsdocs-8080-tcp",
"containerPort": 8080,
"hostPort": 8080,
"protocol": "tcp",
"appProtocol": "http"
}
],
"essential": true,
"environment": [],
"environmentFiles": [],
"mountPoints": [
{
"sourceVolume": "ecsdocs-volume",
"containerPath": "/app/license",
"readOnly": true
}
],
"volumesFrom": [],
"ulimits": [],
"logConfiguration": {
"logDriver": "awslogs",
"options": {
"awslogs-create-group": "true",
"awslogs-group": "/ecs/",
"awslogs-region": "us-east-1",
"awslogs-stream-prefix": "ecsdocs"
},
"secretOptions": []
},
"healthCheck": {
"command": [
"CMD-SHELL",
"curl -f http://localhost:8080/healthz || exit 1"
],
"interval": 30,
"timeout": 5,
"retries": 3,
"startPeriod": 60
}
}
],
"family": "ecsdocs-task",
"taskRoleArn": "arn:aws:iam::807274709480:role/ecsTaskExecutionRole",
"executionRoleArn": "arn:aws:iam::807274709480:role/ecsTaskExecutionRole",
"networkMode": "awsvpc",
"revision": 30,
"volumes": [
{
"name": "ecsdocs-volume",
"efsVolumeConfiguration": {
"fileSystemId": "fs-0be40ac32875f47b4",
"rootDirectory": "/"
}
}
],
"status": "ACTIVE",
"requiresAttributes": [
{
"name": "ecs.capability.execution-role-awslogs"
},
{
"name": "com.amazonaws.ecs.capability.ecr-auth"
},
{
"name": "com.amazonaws.ecs.capability.task-iam-role"
},
{
"name": "ecs.capability.container-health-check"
},
{
"name": "ecs.capability.execution-role-ecr-pull"
},
{
"name": "com.amazonaws.ecs.capability.docker-remote-api.1.18"
},
{
"name": "ecs.capability.task-eni"
},
{
"name": "com.amazonaws.ecs.capability.docker-remote-api.1.29"
},
{
"name": "com.amazonaws.ecs.capability.logging-driver.awslogs"
},
{
"name": "ecs.capability.efsAuth"
},
{
"name": "com.amazonaws.ecs.capability.docker-remote-api.1.19"
},
{
"name": "ecs.capability.efs"
},
{
"name": "com.amazonaws.ecs.capability.docker-remote-api.1.25"
}
],
"placementConstraints": [],
"compatibilities": [
"EC2"
],
"requiresCompatibilities": [
"EC2"
],
"cpu": "1024",
"memory": "14336",
"runtimePlatform": {
"cpuArchitecture": "X86_64",
"operatingSystemFamily": "LINUX"
},
"registeredAt": "2023-08-11T16:56:34.891Z",
"registeredBy": "arn:aws:iam::807274709480:user/bryan",
"tags": []
}17. Create ECS Service
In order to run the Private AI De-identification container in the ECS Cluster, we will define an ECS Service to maintain a healthy number of containers.
- Navigate to the “Amazon Elastic Container Service > Clusters” dashboard, select the previously created cluster.
-
From the “Services” table, click the Create button.
- For “Environment”, select the “Capacity provider strategy” compute option to use the EC2 underlying infrastructure.
- Leave the “Capacity provider strategy” with the defaults.
- For “Deployment configuration”, select the “Service” Application type, the task definition family previously created, and enter a Service name.
- Optional - Specify values for “Desired tasks”, “Min running tasks %”, “Max running tasks %”, and “Deployment failure detection” settings. For the purposes of this document, we will leave the “Desired tasks” at 1, and the other options as default.
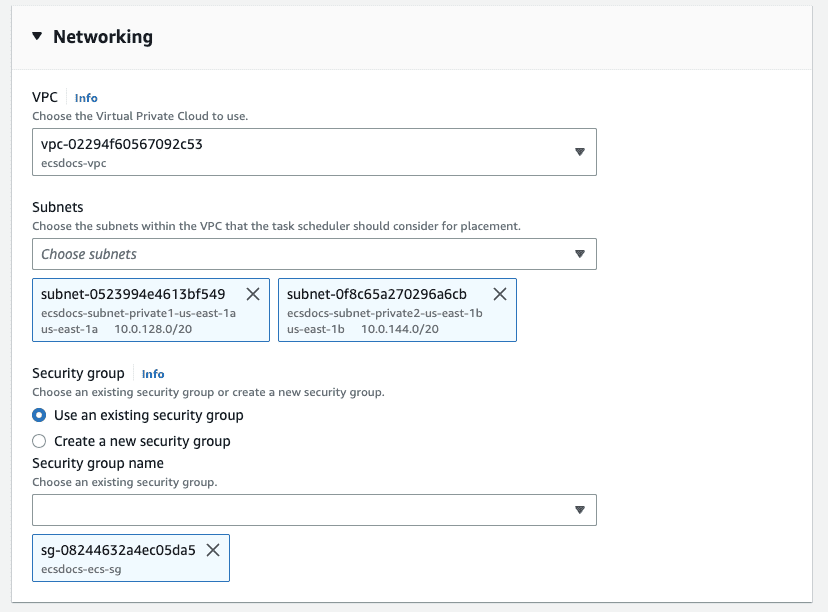
- For “Networking”, under “Subnets”, remove the public subnets.
-
For “Networking”, under “Security group” remove the default security group and add the previously created security group for ECS.
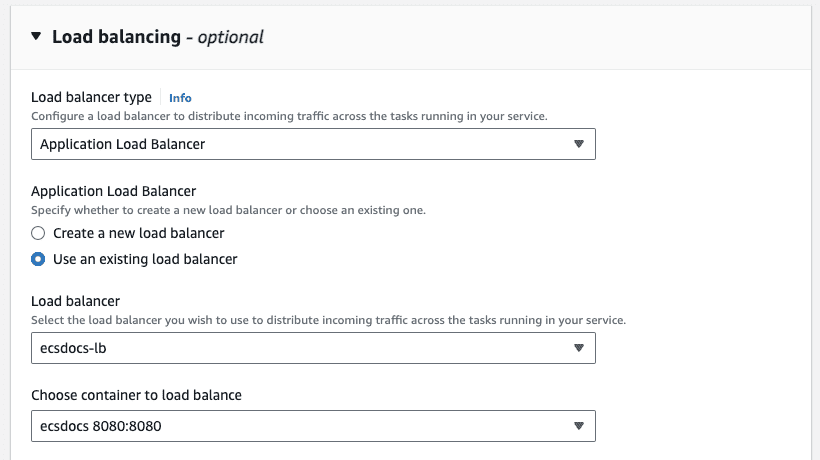
- For “Load balancing - optional” leave the default “Load balancer type” to “Application Load Balancer”.
- For “Application Load Balancer” select “Use an existing load balancer”.
- For “Load balancer” select the load balancer created in a previous section.
-
For “Choose container to load balance” leave the default container.
- For “Listener” select "Use and existing listener" and select the listener created in a previous section.
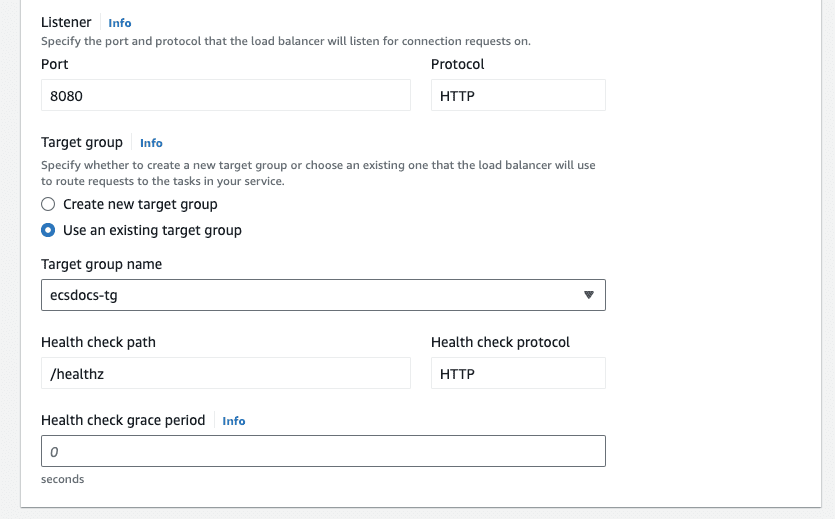
- For “Target group” select “Use an existing target group”.
- For “Target group name” select the target group created in a previous section.
-
Optional - Leave the default “Health check grace period” of 0 or change as desired.
- Optional - Leave the default “Service auto scaling - optional”.
- Optional - Leave the default “Task Placement”.
- Optional - For “Tags - optional” enter any appropriate tags as required.
- Click Create.
-
Once the service has finished deploying, check the Tasks tab to find the deployed ECS task instance.
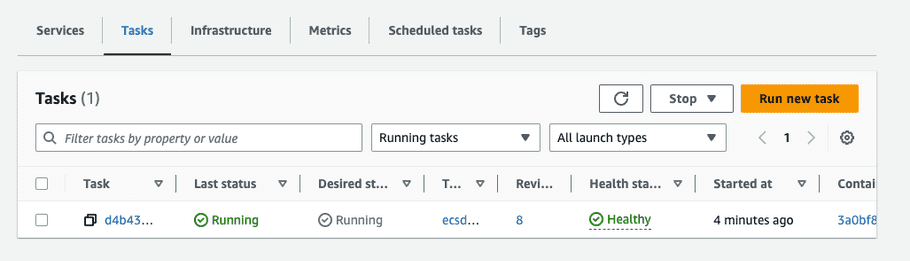
-
Click on the task and scroll down to the “Configuration” section of the task to find the “Private IP” address.
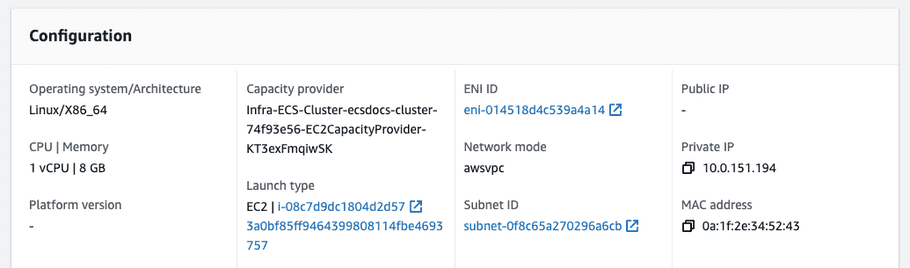
- Copy the Private IP address.
- SSH into the Bastion Host created in a previous step.
-
Run the following command to test that the Private AI De-identification service is reachable. You should receive a JSON object response which contains the app version, such as below.
curl http://10.0.151.194:8080/ {”app_version”:”3.2.2-cpu”} - Repeat the steps above for any additional service tasks defined in the cluster.
- Navigate to the “EC2” dashboard and select “Load Balancers” from the left menu.
- Select the load balancer created in a previous section.
- Copy the DNS name from the load balancer.
-
If you deployed an internal-facing load balancer, return to the SSH console for the Bastion Host. If you deployed an internet-facing load balancer, open an SSH prompt on your computer. Run the following command to ensure that the service tasks are reachable via the load balancer.
curl http://ecsdocs-lb-207344012.us-east-1.elb.amazonaws.com/ {”app_version”:”3.3.2-cpu”}